
We set the standard for cybersecurity governance, risk management and regulatory compliance services within the financial sector. Our defensive services, delivered by our dedicated Blue Team, integrate bespoke technology solutions with deep industry knowledge, ensuring your firm navigates the cybersecurity landscape confidently, meets compliance demands, and confidently counters emerging threats.
We offer unparalleled WISP development services tailored to fit your unique technology and security footprint while being aligned with industry frameworks like NIST CSF and CIS CSC. Our expertly crafted WISPs are designed to be intuitive, easily-maintainable and actionable, allowing you to navigate the complex landscape of regulatory compliance confidently.
Navigate the intricate web of regulatory requirements with ease. Our WISPs are engineered to help your organization comply with stringent standards from the SEC, FCA, DORA and NYDFS 23 NYCRR 500, ensuring you meet or exceed the necessary legal and regulatory benchmarks.
From administrative to technical defenses, our WISPs encompass a wide array of safeguards, including data classification, risk management, physical security controls, incident response, business continuity, generative AI acceptable use, and more. This holistic approach ensures that every aspect of your organization's security is fortified.
Our WISPs are customized to your organization's unique needs, crafted for clarity and ease of understanding, ensuring that policies are not only comprehensive but also straightforward to implement and keep up-to-date.
With our WISPs, your organization gains more than just a policy document, you receive a complete ecosystem of security processes, including task lists, incident response plans, and business continuity strategies, all within our Panoptix Cybersecurity Dashboard.
In the interconnected world of business, your cybersecurity posture is only as strong as the weakest link in your supply chain. Our Third-Party Risk Management and Vendor Due Diligence solutions are designed to fortify your defenses by ensuring that your vendors' cybersecurity measures meet and exceed industry standards. Leveraging robust evaluation frameworks such as CAIQ, SIG and AITEC-AIMA, our vendor due diligence questionnaires provide a comprehensive assessment of your vendors' cybersecurity maturity.
Utilize industry standard frameworks complemented by custom questions to gain deep insights into your vendors' cybersecurity practices, ensuring a thorough evaluation tailored to your unique requirements.
Our innovate pricing for assessing unique vendors offers unparalleled value. You won't pay extra for any vendors we've recently assessment, a testament to the benefits of being part of our ecosystem. This model is designed to encourage comprehensive due diligence without the worry of escalating costs.
All vendor due diligence data is effortlessly integrated into our cutting-edge Cybersecurity Dashboard. This integration provides you with centralized access and visibility into your due diligence activities, streamlining your risk management processes and enhancing your ability to make informed decisions about your vendors.
Being part of our cybersecurity ecosystem ensures you're always informed about the security posture of your vendors thanks to our continuously updated assessments. This proactive approach to vendor risk management enables you to understand your vendors' security posture without having to ask.
Our vCISO service offers a comprehensive, white-glove approach to safeguarding your organization and taking care of all your cybersecurity regulatory compliance requirements. Unlike traditional offerings, our vCISO service provides not just one individual, but an entire dedicated cybersecurity team.
Our multidisciplinary cybersecurity team ensures all aspects of managing your cybersecurity program are covered, from strategic compliance advisory to technical implementation, offering unparalleled depth and breadth of expertise. Our commitment to quality and expertise is reflected in our team of full-time employees based in the US and UK, holding numerous certifications such as CISSP, GRCP, Security+, CySA+, CSAP, CNVP, CIOS, CSIS, OSCP, and more.
With our approach to building your cybersecurity initiatives plan for the entire year, your organization will benefit from proactive management of cybersecurity measures and risk mitigation. This forward-looking strategy ensures that your security posture is not only reactive but also anticipatory, preparing you for emerging threats and compliance requirements. Our white-glove services also include answering due diligence questionnaires from investors, LPs, partners, and auditors to reinforce trust with all stakeholders.
Our vCISO team works hand-in-hand with other Abacus teams and your internal IT department if applicable to ensure a cohesive approach to managing cybersecurity risks. This collaboration includes technical strategy, validating remediations, and updating your risk register, ensuring that your cybersecurity measures are both effective and verifiable.
Through our Panoptix Cybersecurity Dashboard, you are given comprehensive visibility into your organization's cybersecurity initiatives, including project progress, timelines, and lead resources. With our unparalleled expertise, proactive management, and commitment to transparency, we ensure that your organization is not just protected, but has a strong cybersecurity compliance posture.
Our Incident Response Table Top Testing services are designed to arm your organization against the ever-evolving landscape of cyber threats by emulating various security incidents. We prepare your team for the unexpected through the simulation of realistic scenarios, including business email compromise (BEC) attacks and ransomware attacks.
We employ a hybrid approach of leveraging our real-world white hat hacker expertise alongside CISA's Table Top Exercise Packages to deliver exercises customized to your organization's security program and technology stack. Our approach equips your team with the knowledge to identify and respond to incidents effectively.
Beyond theoretical knowledge, our table top testing provides hands-on practice and step-by-step guidance to improve your security posture. This ensures you are thoroughly prepared to respond to threats swiftly and efficiently in the future.
Our testing exercises are designed to enhance coordination and communication among your incident response team. By working through simulated attacks together, team members learn how to respond to actual incidents and are provided an incident response management framework within our Panoptix Cybersecurity Dashboard.
Our testing ensures your organization meets cybersecurity compliance requirements set by regulatory bodies such as the SEC, FCA and DORA. By identifying and addressing weaknesses in your incident response plan, we not only aid in achieving compliance by also significantly reduce your risk profile.
Our PortCo Advisory Services for Private Equity firms represent a paradigm shift in how investments are protected in the digital age. Our suite of specialized cybersecurity services are designed to safeguard portfolio companies from the dual threats of cyber incidents and regulatory non-compliance across all major industries, including financial services, healthcare, industrial manufacturing, technology, retail and energy utilities.
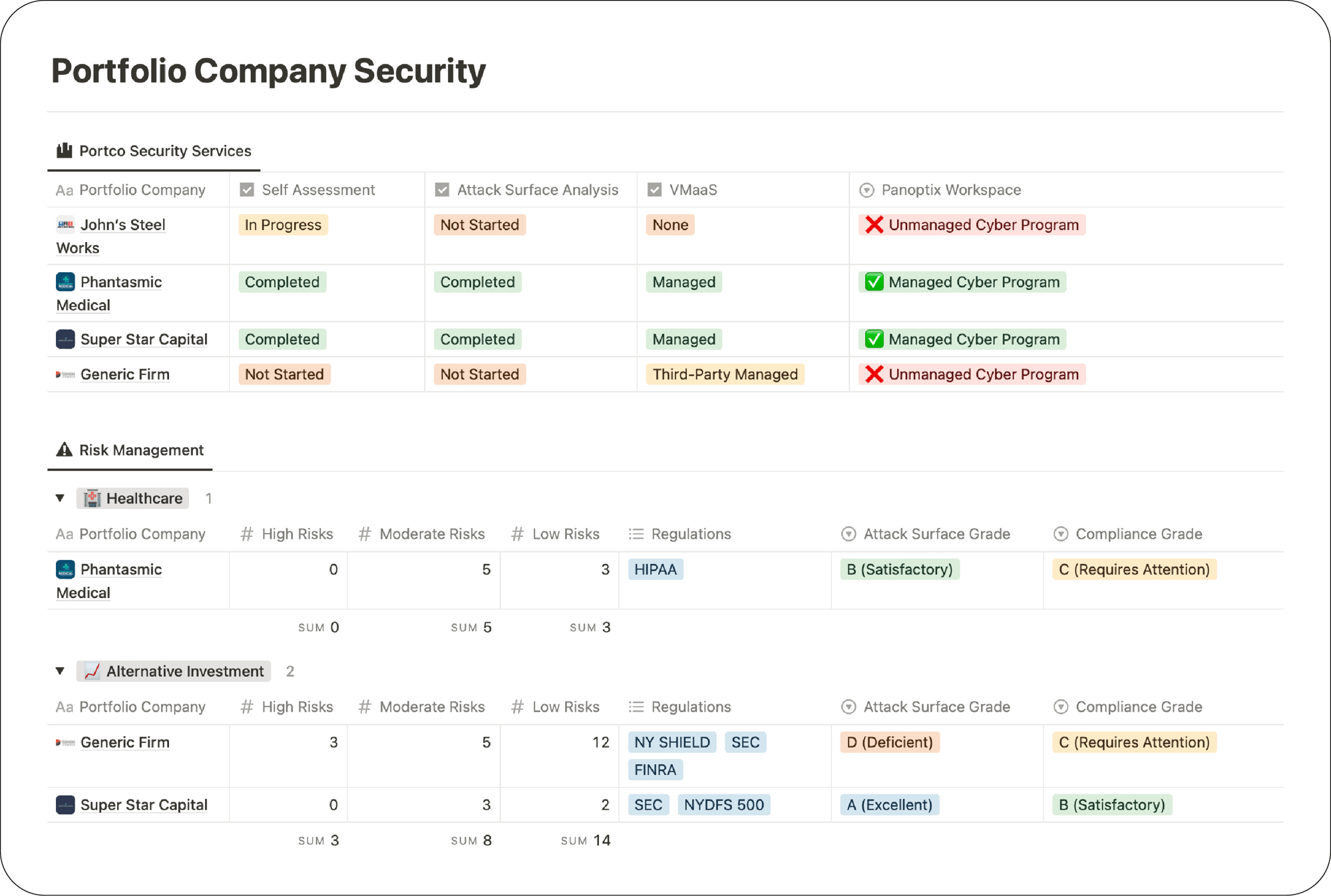
Through our Panoptix Cybersecurity Dashboard, we offer PE firms a comprehensive view for managing and monitoring the cybersecurity health of their portfolio companies. This unparalleled visibility into each company's cybersecurity posture and regulatory compliance status empowers PE firms to proactively understand and address vulnerabilities, safeguarding their investments from security breaches and legal ramifications.
Our external and internal attack surface analysis services employ both advanced agentless and agent-based scanning techniques to understand the security posture of a portfolio company. Our approach allows us to uncover vulnerabilities across a wide array of company assets and provide actionable risk reduction recommendations to ensure that portfolio companies maintain a strong defense against cyber threats.
Our expertise is a pivotal asset for PE firms trying to understand the complex cybersecurity and compliance posture of potential investment targets. We strategically evaluate the maturity of an investment target's security program to empower PE firms to make well-informed decisions as well as understand hidden cybersecurity deficiencies that could pose significant post-acquisition financial and operational risks.
Our Written Information Security Program development services are designed to cater to the unique cybersecurity needs and business goals of each portfolio company. Recognizing the diversity within portfolio companies, we take into account the specific industry, size and operational complexity of each company, ensuring that the cybersecurity framework is both effective and scalable, capable of evolving as the company grows.
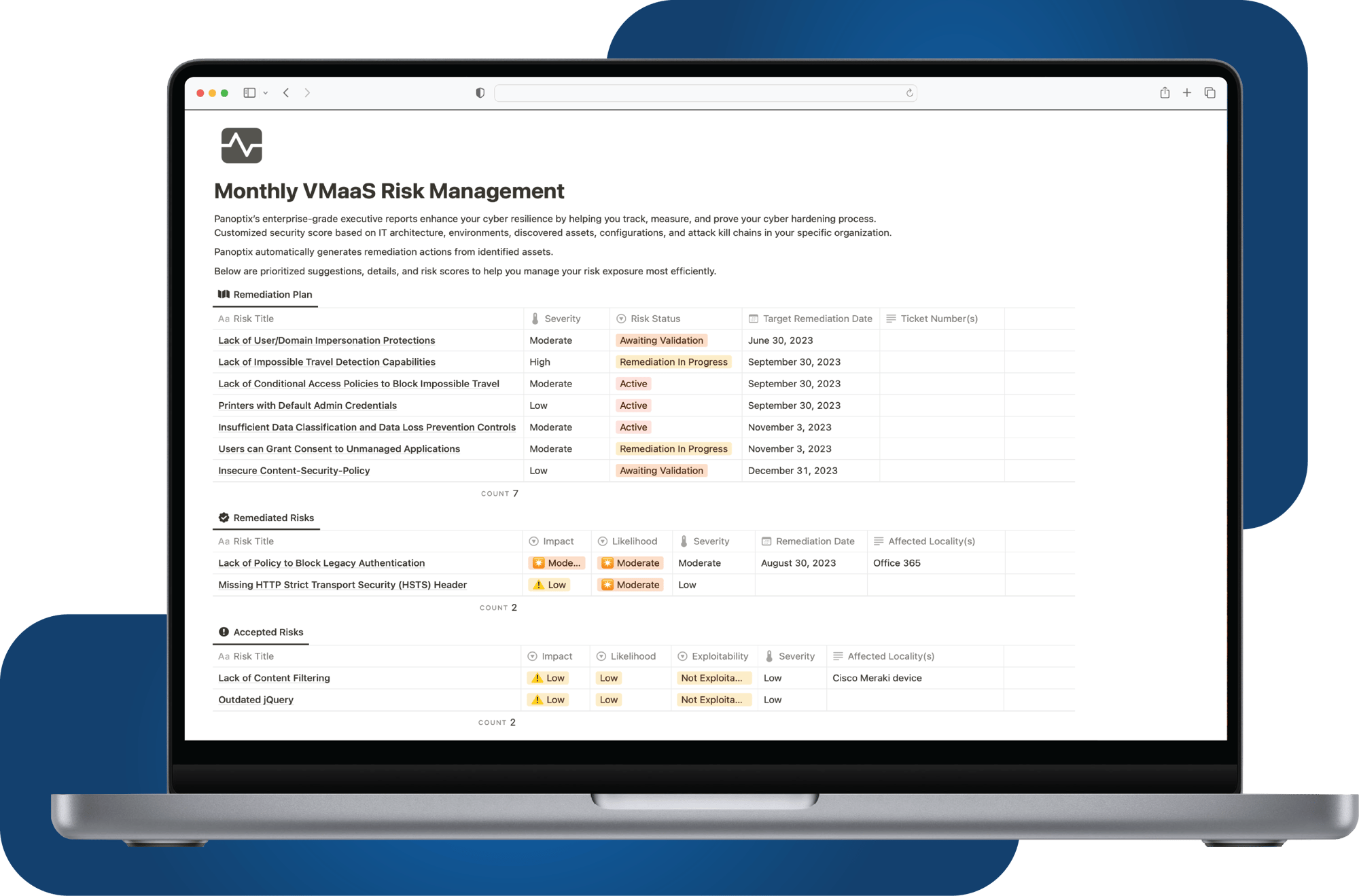
We provide a transparent cybersecurity and risk management dashboard, empowering you to continuously monitor, measure and improve your organization's security posture. Data from our governance and risk management services automatically funnels into your dashboard, allowing you to track your cybersecurity efforts in one place in realtime.